Essential Tips for Securing Your IoT Devices: A Guide to Vulnerability Management
6 Mins Read
Published on: 06 April 2023
Last Updated on: 21 November 2024

toc impalement
The Internet of Things (IoT) has completely overhauled our interaction with recent technology. In particular, it has made our lives more convenient and efficient, from smart homes to wearable devices. However, as the number of Internet of Things devices grows, so does the risk of security breaches.
This article explains vital tips for securing IoT devices through vulnerability management processes. Regardless of the size or nature of your business, you need to invest in security for your systems.
Read on to learn what it takes to prevent attacks, manage risks, or reduce the extent of damage in case your systems suffer a major attack.
Here are 9 Tips for Securing Your IoT Devices
Arguably, the risk of security breaches increases along with IoT expansion. The more we enjoy the benefits and features of modern-day IoT devices, the more threats become serious.
Your internet-connected devices often gather and share data. If you do not protect them well, attackers can gain access anytime.
Protecting your devices and systems means implementing various security measures. Moreover, you may use a few or a combination of different security measures. Subsequently, Your choice of vulnerability management measures depends on your system’s types and the nature of threats.
Here are nine helpful tips for securing your IoT devices:
1) Identify Loopholes and Potential Vulnerabilities

A risk assessment is the first step in securing your IoT devices. As a result, this will enable you to prioritize which devices need the most attention. Moreover, it also helps you find any potential system vulnerabilities and weaknesses.
Note the following when doing your assessment:
- A security breach’s possible effects
- The risk of an attack
- The sorts of data your devices collect and share
A risk assessment can help you create a strategy first to address the most pressing vulnerabilities. As a result, you can then plan with the information at hand and secure your systems.
Hence, do not wait for an attack; get the assessment done ASAP. This is one of the best and most prominent tips on securing IoT devices.
2) Understand Vulnerability Management Steps
What is vulnerability management? It is an ongoing process. It necessitates continuous monitoring, assessment, and remediation to ensure your systems remain secure and safe from attacks. To do all these, you need to understand its steps, including the following:
a) Vulnerability Identification
The first step in vulnerability management is to identify system vulnerabilities. You can accomplish this with various tools and techniques, including vulnerability scanners, penetration testing, and manual testing. The goal is to identify all vulnerabilities in the system, including software flaws, configuration flaws, and human errors.
b) Assessment
Once identified, vulnerabilities must be assessed to determine their impact and likelihood of exploitation. This entails analyzing the vulnerability to determine how far it can be exploited, what data or systems it may affect, and what level of access it may provide to attackers.
c) Prioritization
Prioritize them based on their severity and likelihood of exploitation. Prioritization assists your organization in concentrating its efforts and resources on the most critical vulnerabilities first.
The severity of a vulnerability is determined by factors such as the potential impact on the system, the ease of exploitation, and the availability of publicly available exploits.
d) Patching
Apply patches or other remediation measures to address the vulnerabilities. Depending on the nature of the vulnerability, patches may take the form of software updates or configuration changes. Note that they must be thoroughly tested before applying patches to production systems.
e) Remediation
Finally, after applying patches, the system must be tested again to ensure the vulnerabilities have been adequately addressed. This includes re-evaluating the vulnerabilities to ensure they are no longer present and confirming that the patches have been applied successfully.
You should also perform continuous monitoring and testing to ensure new vulnerabilities are identified and addressed immediately.
3) Protect Your Data Using Encryption

Data is transformed into a code that can only be cracked with a unique key through encryption. You can be sure that the data your IoT devices collect and share is secure because of encryption. Even if it falls into the wrong hands, it is safe.
Although many IoT devices already have encryption capabilities, you may encrypt your data. Use encryption software before sending it to the cloud or another device.
4) Avoid Third-Party Apps and Devices
Third-party hardware and software can be a security concern if you do not evaluate them thoroughly. So, investigate any third-party hardware or apps before integrating them with your IoT devices. That is the only way to guarantee their security and reliability.
Please avoid using software or hardware known to have security flaws. Most importantly, always check the permissions needed before installing any apps or software on your devices. Any third-party device or app can aid infiltration into your systems.
5) Ensure Your Internet Devices Are Up-To-Date
Maintaining the most recent software updates and patches on your IoT devices is one of the most crucial things you can do to keep them secure. Indeed, it is essential to check for updates routinely. Manufacturers frequently provide patches to address security flaws.
Many gadgets also offer an auto-update capability that may enable you to ensure that your devices are always running the most recent software. Check for such updates as often as possible if your systems do not update automatically.
6) Implement Preventive Monitoring of Your Devices

You may prevent security breaches from happening by monitoring your IoT devices and taking appropriate action. You may follow your devices using various monitoring tools, including SIEM (Security Information and Event Management) programs and intrusion detection systems.
Keep an eye on your devices to detect any unexpected activity immediately and take precautions to reduce security threats.
7) Learn and Share Information with Colleagues
Education about security dangers and recommended practices is one of the most crucial things you can do to protect your IoT devices. Be abreast of the most recent security risks and weaknesses, and let anyone who uses your devices know about them. Ensure that everyone using your devices knows the value of security and how to adhere to best practices for managing vulnerabilities.
8) Always Disable Any Unused Features in Your IoT Devices
Numerous IoT devices include capabilities that, while you might not require or utilize them, could nonetheless be a security issue. For instance, a smart thermostat with a built-in camera that you would never use might be hacked and used to spy on you.
You may lessen the attack surface of your devices and increase their security by deactivating any unnecessary functionalities. Do this for all your apps and devices. That means you need to explore all their features when you acquire them.
9) Consider Using a Virtual Private Network for Security
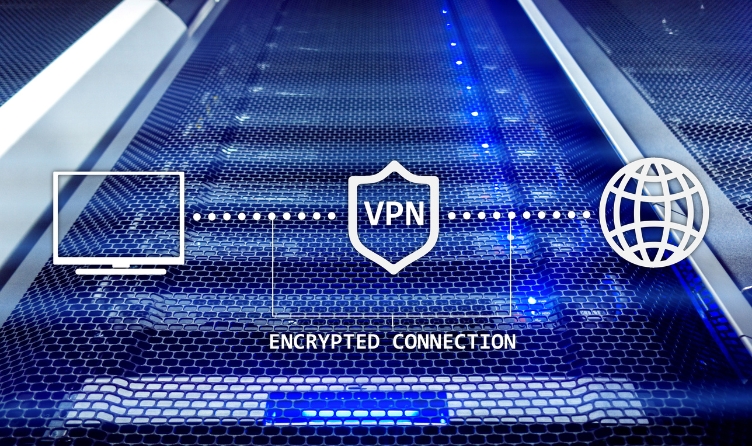
Your IoT devices are only as secure as the network to which they are linked. To secure your network, use a strong password and consider using a virtual private network (VPN). Also, turn off any unused network ports. Further, consider network segmentation to isolate your IoT devices from other network devices.
Conclusion
In conclusion, using a vulnerability management system to secure your IoT devices requires a combination of technical safeguards and industry standards.
Any device you connect to the internet is vulnerable, and you must secure it. The data you store and share is vital. Any mistake can cause huge losses. So, you have to protect your IoT devices effectively. As you have learned in this article, you can significantly lower the risk of a security breach by performing a risk assessment.
Therefore, you must understand how to secure IoT devices, such as keeping your devices up-to-date, changing default passwords, utilizing two-factor authentication, securing your network, monitoring your devices, etc.
Stay safe!
Read Also:

















Comments Are Closed For This Article